Instagram is building non-SMS 2-factor auth to thwart SIM hackers
Instagram is building non-SMS 2-factor auth to thwart SIM hackers
Instagram is building non-SMS 2-factor auth to thwart SIM hackers
Hackers can steal your phone number by reassigning it to a different SIM card, use it to reset your passwords, steal your Instagram and other accounts, and sell them for Bitcoin. As detailed in a harrowing Motherboard article today, Instagram accounts are especially vulnerable because the app only offers two-factor authentication through SMS that delivers a password reset or login code via text message.
But now Instagram has confirmed to TechCrunch that it’s building non-SMS two-factor authentication system that works with security apps like Google Authenticator or Duo. They generate a special code that you need to login that can’t be generated on a different phone in case your number is ported to a hacker’s SIM card.
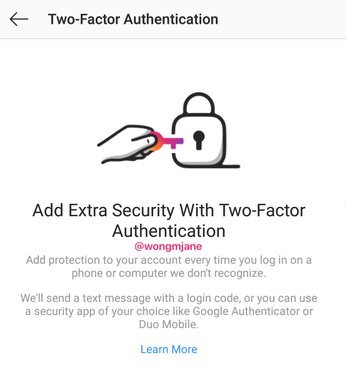
Buried in the Instagram Android app’s APK code is a prototype of the upgraded 2FA feature, discovered by frequent TechCrunch tipster Jane Manchun Wong. Her work has led to confirmed TechCrunch scoops on Instagram Video Calling, Usage Insights, soundtracks for Stories, and more.
When presented with the screenshots, an Instagram spokesperson told TechCrunch that yes, it is working on the non-SMS 2FA feature, saying “We’re continuing to improve the security of Instagram accounts, including strengthening 2-factor authentication.”
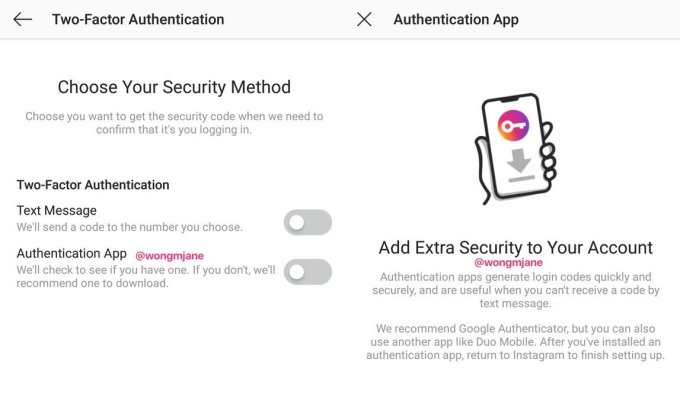
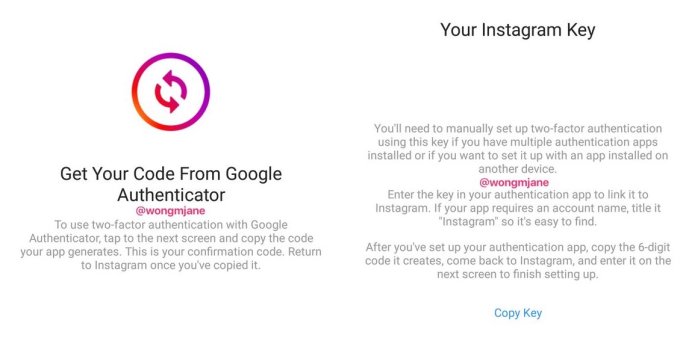
Instagram actually lacked any two-factor protection until 2016 when it already had 400 million users. In November 2015, I wrote a story titled “Seriously. Instagram needs two-factor authentication.” A friend and star Instagram stop-motion animation creator Rachel Ryle had been hacked, costing up a lucrative sponsorship deal. The company listened. Three months later, the app began rolling out basic SMS-based 2FA.
But since then, SIM porting has become a much more common problem. Hackers typically call a mobile carrier and use social engineering tactics to convince them they’re you, or bribe an employee to help, and then change your number to a SIM card they control. Whether they’re hoping to steal intimate photos, empty cryptocurrency wallets, or sell desireable social media handles that like @t or @Rainbow as Motherboard reported, there are plenty of incentives to try a SIM porting attack. This article outlines how you can take steps to protect your phone number.
Hopefully as knowledge of this hacking technique becomes more well known, more apps will introduce non-SMS 2FA, mobile providers will make it tougher to port numbers, and users will take more steps to safeguard their accounts. As our identities and assets increasingly go digital, its pin codes and authenticator apps, not just deadbolts and home security systems, that must become a part of our everyday lives.
from Mobile – TechCrunch https://ift.tt/2mpjUWH
via Blogger https://ift.tt/2Lkx6ui
July 18, 2018 at 03:06AM
via Blogger https://ift.tt/2utw31m
July 18, 2018 at 05:33AM
via Blogger https://ift.tt/2LrGkBD
July 18, 2018 at 08:34AM
via Blogger https://ift.tt/2Lm749Q
July 18, 2018 at 11:33AM



0 Comments